Cybereason Addon For Splunk
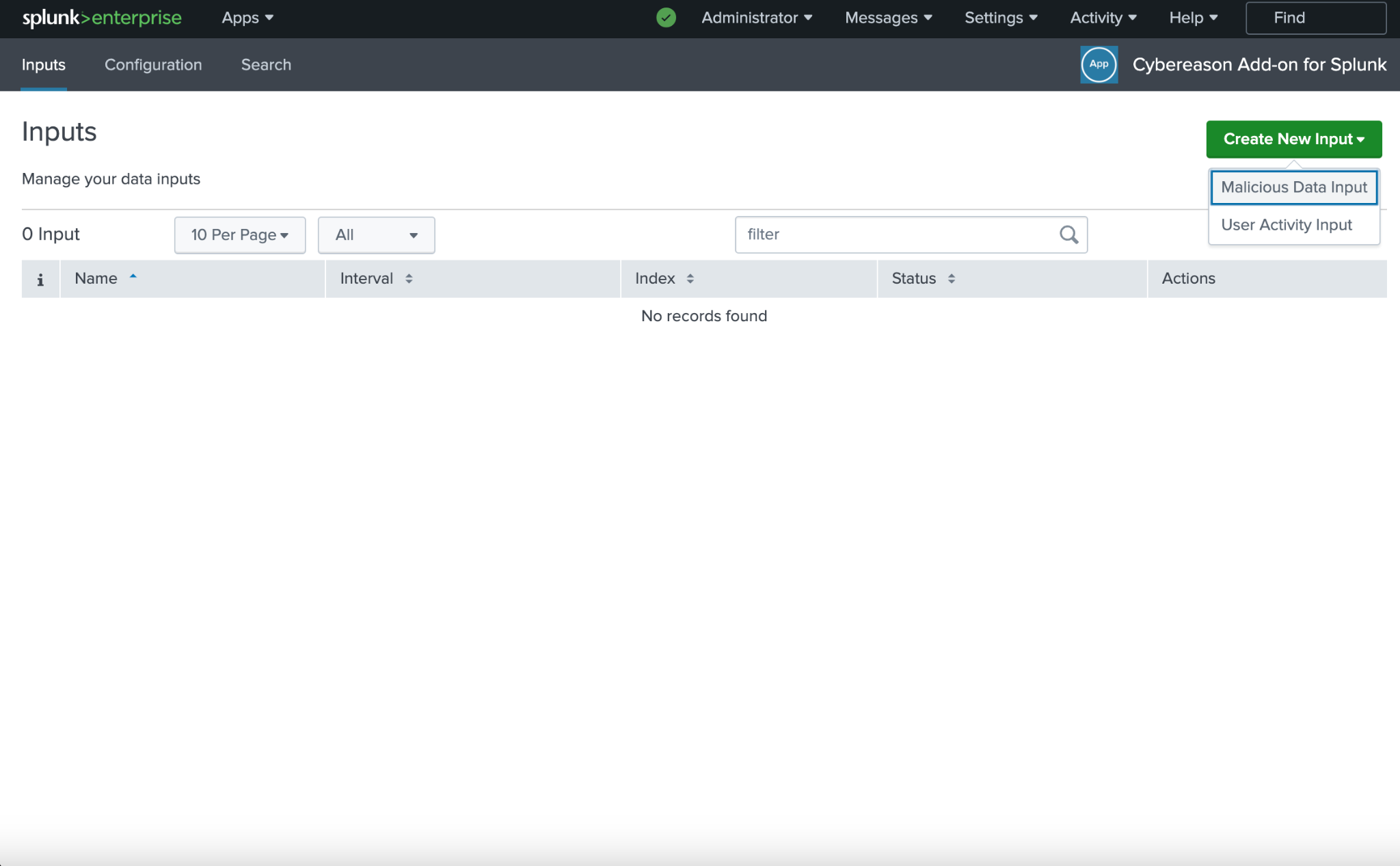
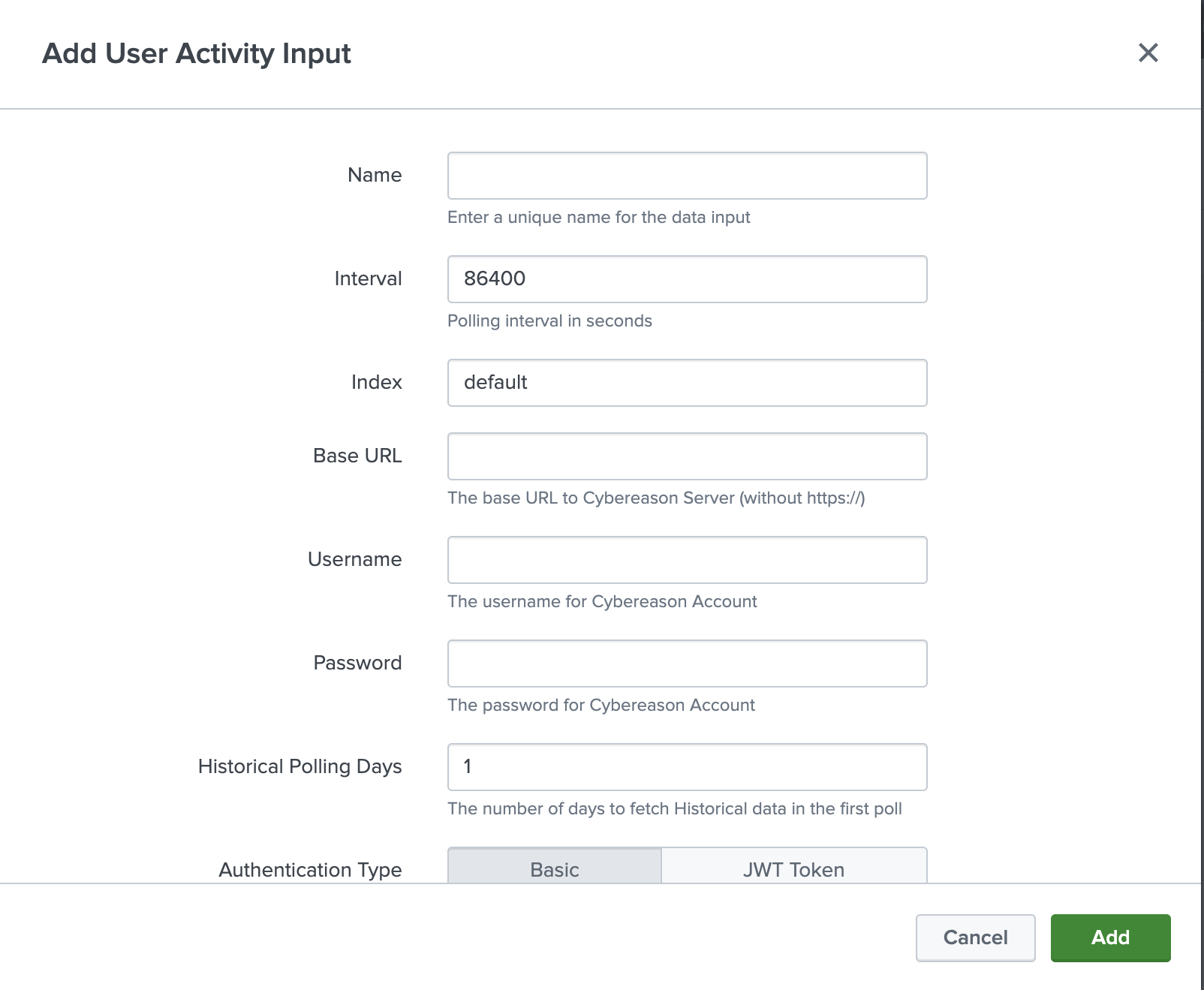
The Cybereason Add On for Splunk enables you to fetch the data from Cybereason AI Hunting Engine and EPP Malop Hunting. The Cybereason AI Hunting Engine automatically asks a complex set of questions of data collected from all of your endpoints at a rate of 8 million calculations per second, 24 hours a day, 7 days a week. This means the solution is continuously hunting on your behalf by asking the same sorts of questions advanced security analysts would ask as they hunt for threats inside an environment. The difference, however, is that the Cybereason malicious activity models run constantly, and continually adapt and evolve according to the data the solution receives and analyzes.
Built by
Latest Version 2.1.20
December 15, 2025
Compatibility
Splunk Enterprise, Splunk Cloud
Platform Version: 9.4, 9.3, 9.2, 9.1, 9.0
CIM Version: 4.x, 3.x
Rating
1
(5)
Log in to rate this app
Support
Developer Supported addon
The Cybereason Add On for Splunk enables you to fetch the data from Cybereason AI Hunting Engine and EPP Malop Hunting. The Cybereason AI Hunting Engine automatically asks a complex set of questions of data collected from all of your endpoints at a rate of 8 million calculations per second, 24 hours a day, 7 days a week. This means the solution is continuously hunting on your behalf by asking the same sorts of questions advanced security analysts would ask as they hunt for threats inside an environment. The difference, however, is that the Cybereason malicious activity models run constantly, and continually adapt and evolve according to the data the solution receives and analyzes.
The data retrieved by the Add On can be consumed by another Splunk app "Cybereason for Splunk"(https://splunkbase.splunk.com/app/4137). The Cybereason for Splunk app enables you to gain deep insight & visibility into your endpoints, detect advanced attacks based on AI hunting and EPP Malop Hunting, and take response actions within Splunk.
Please note:
For Cybereason 21.1 environment, "Responder L1" role needed for fetching Malops.
For Cybereason 21.1 environment, Admin role needed for fetching User Action Logs.
Notice: Cybereason On-premise users should not upgrade the Cybereason Add-on for Splunk beyond v2.1.15. Higher versions are incompatible with Cybereason on-prem installations and will cause the application to break.
Categories
IT Operations, Security, Fraud & Compliance
Created By
Cybereason
Type
addon
Downloads
4,299
Splunk Answers
Ask a question about this app listing(Opens new window)Resources
Log in to report this app listing