Cloud Security Monitoring (CSM)
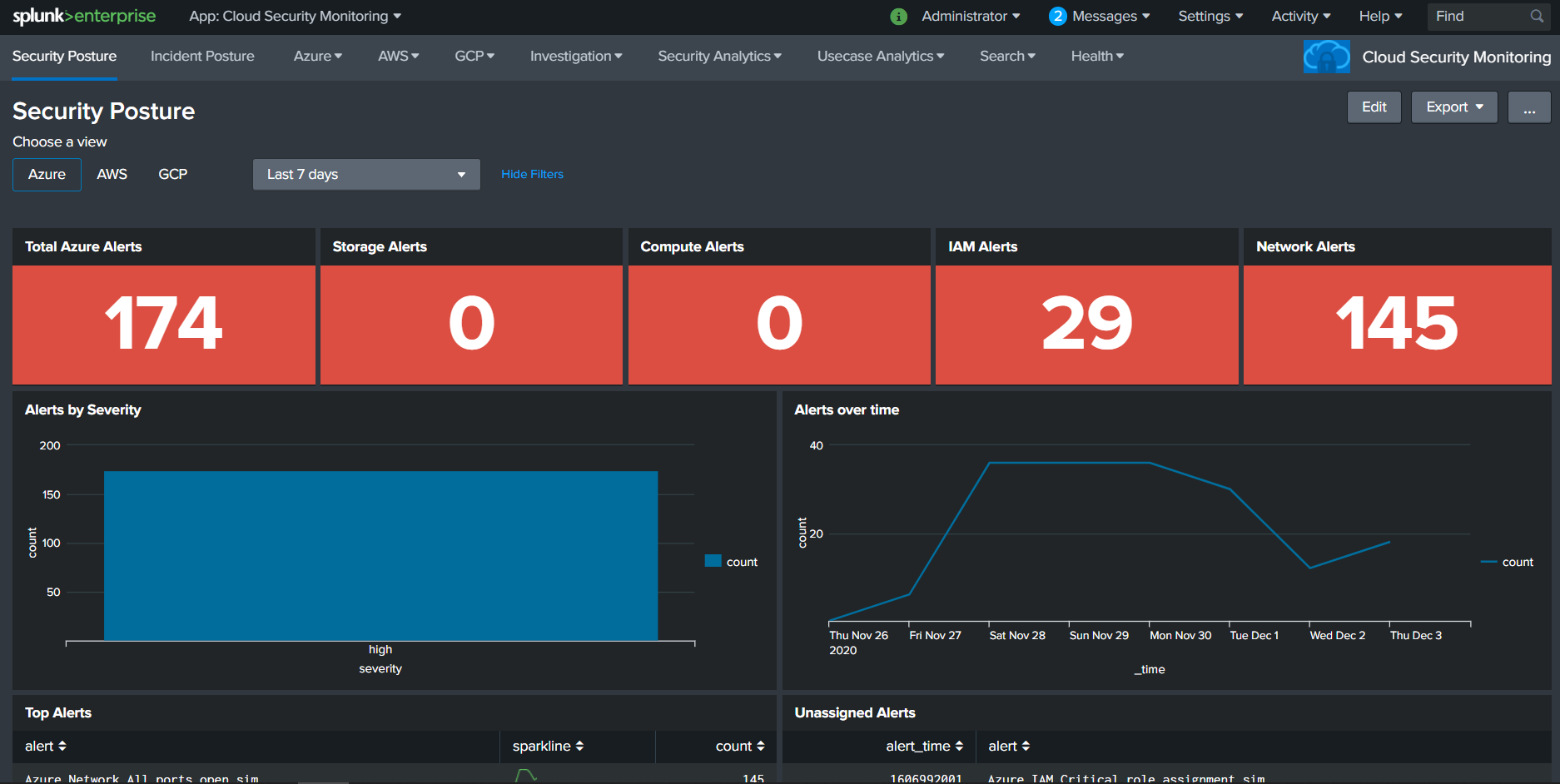
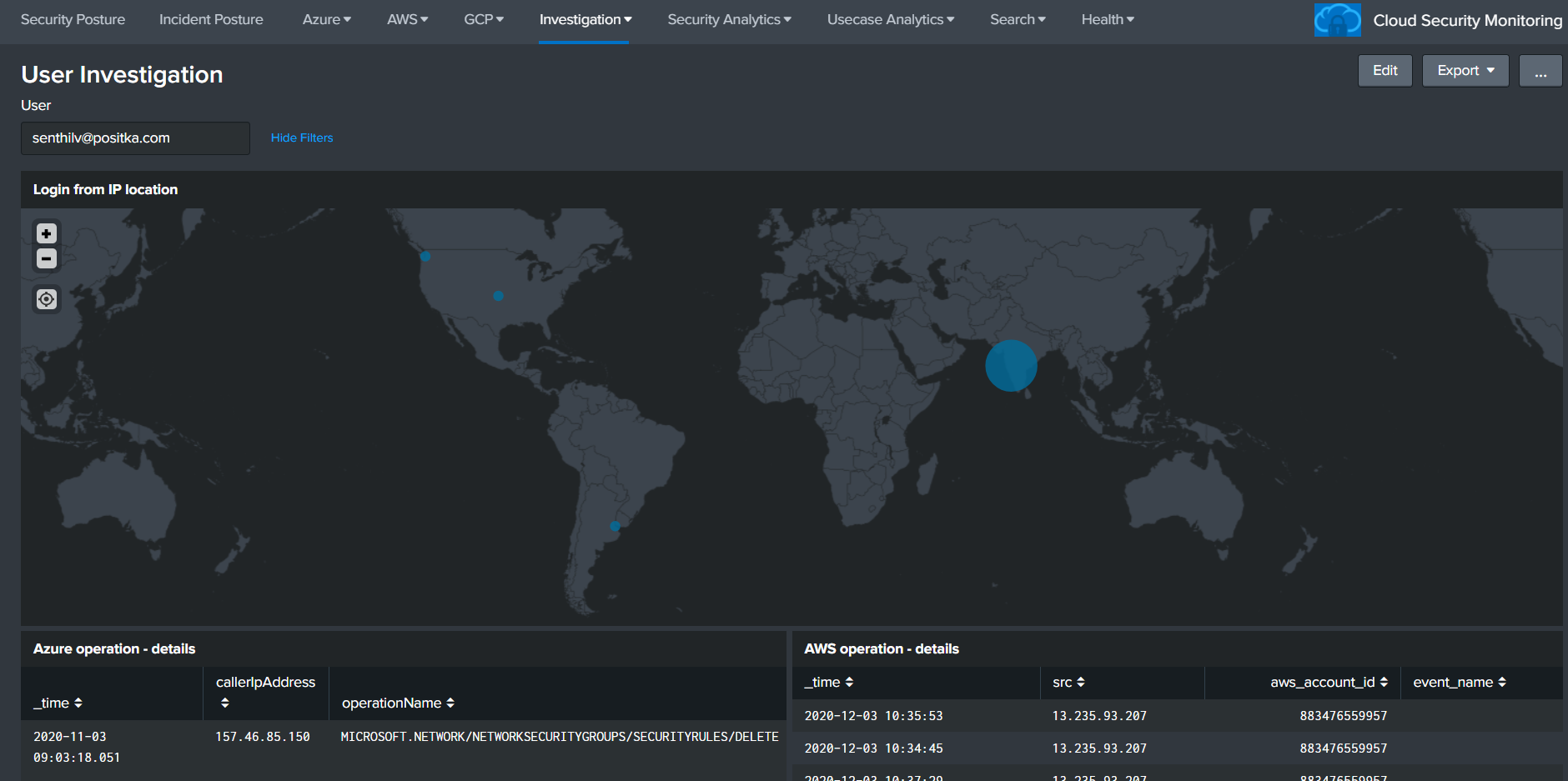
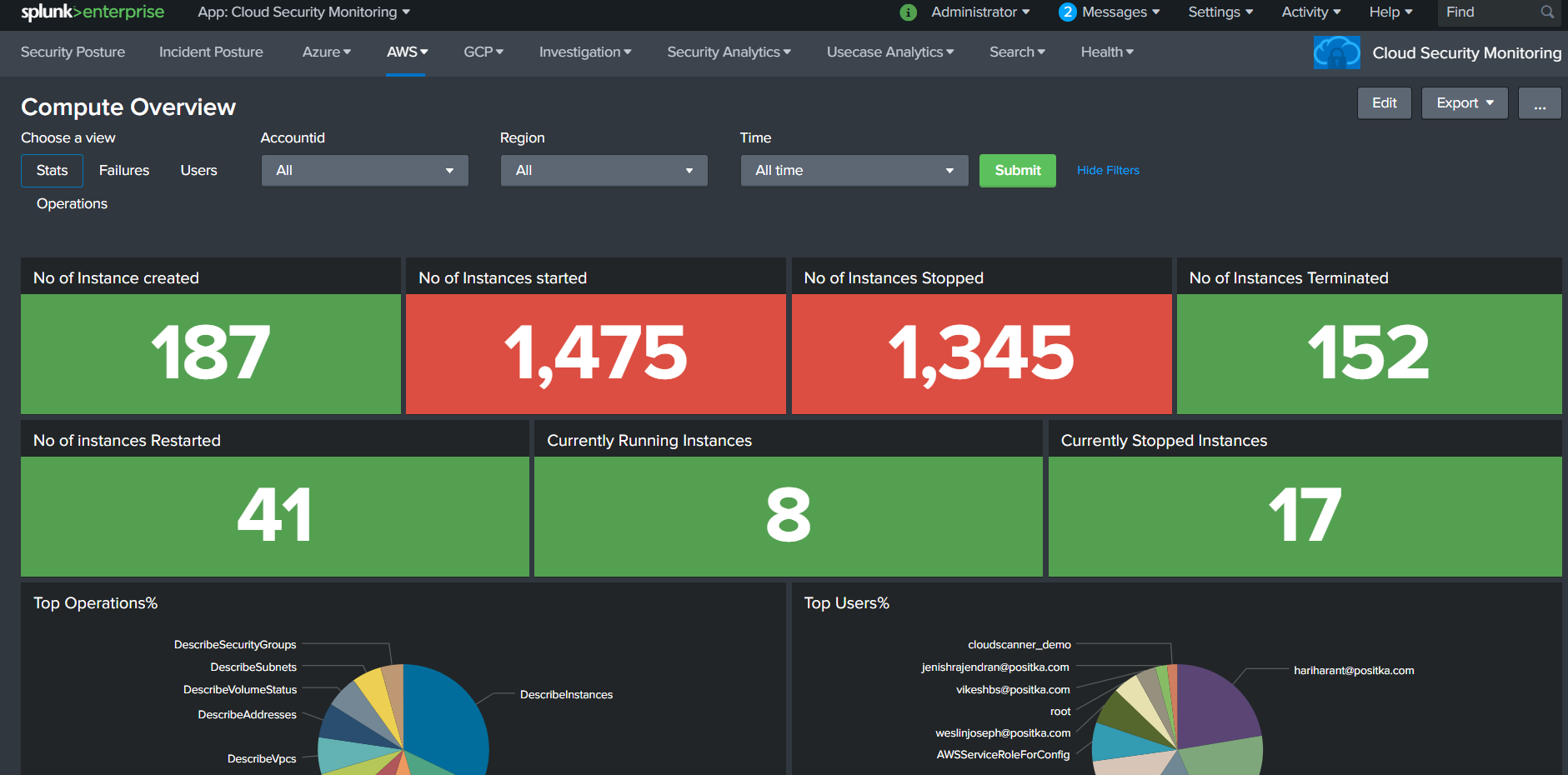
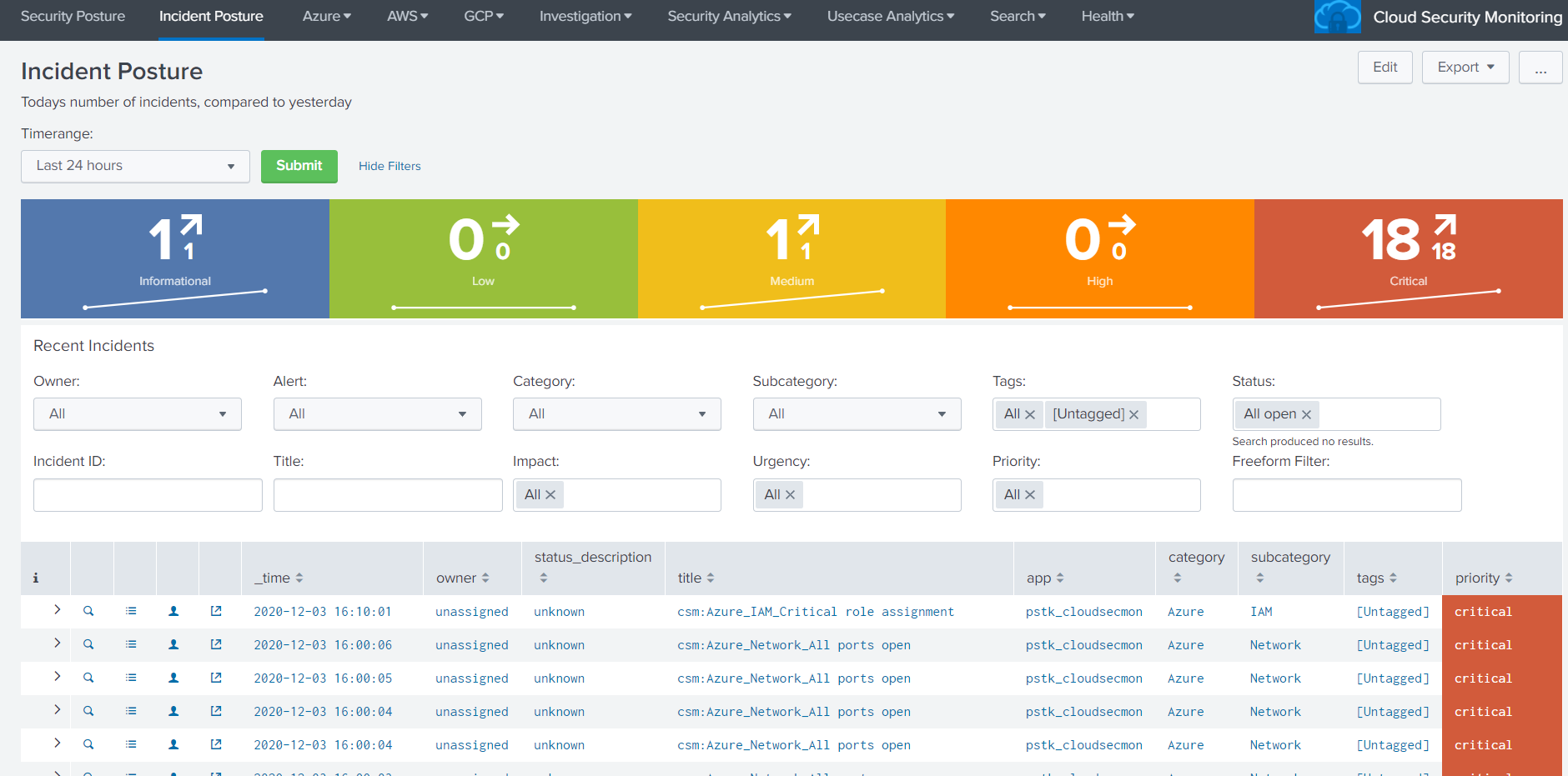
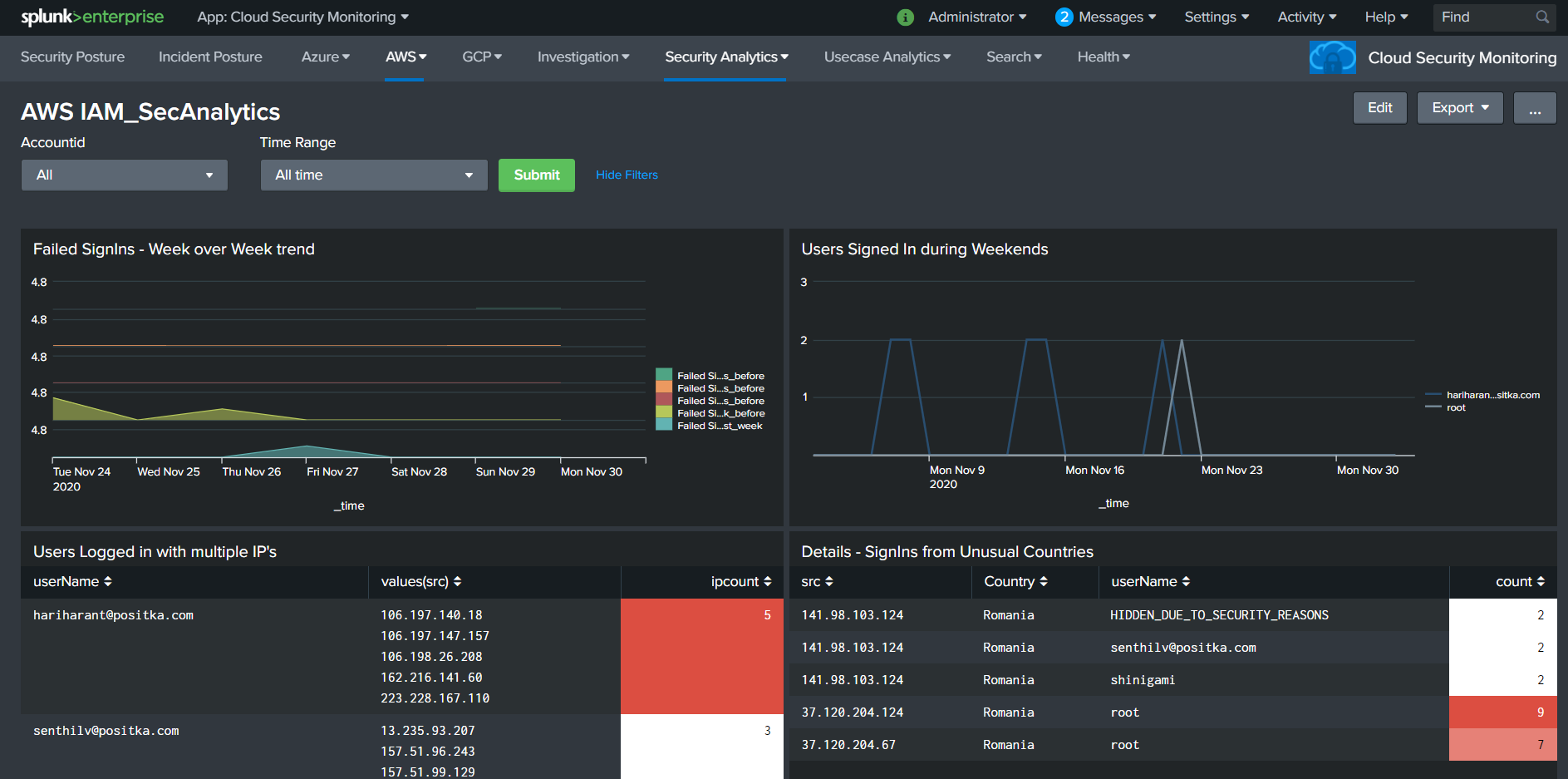
Cloud Security Monitoring is an application which is built on top of Splunk that provides visibility to the organization's Cloud infrastructure. - The Positka Cloud Security Monitoring App gives you critical insights into your AWS and Azure accounts to analyse and visualize data from numerous services like Compute, Storage, IAM and Network - The Positka Cloud Security Monitoring solution helps security teams streamline security operations for organizations of all sizes and levels of expertise. - It helps you gain end-to-end visibility across your cloud environment for the SOC Analyst to detect, investigate, and respond to internal and external cloud-based threats which offers pre-packaged dashboards, correlation rules, and incident response workflows to help SOC teams analyse, investigate and respond to alerts.
4
(7)
Categories
Created By
Type
Downloads
Splunk Answers
Ask a question about this app listing(Opens new window)Resources