This app is archived.
Nimbus (CA UIM) add-on in Splunk
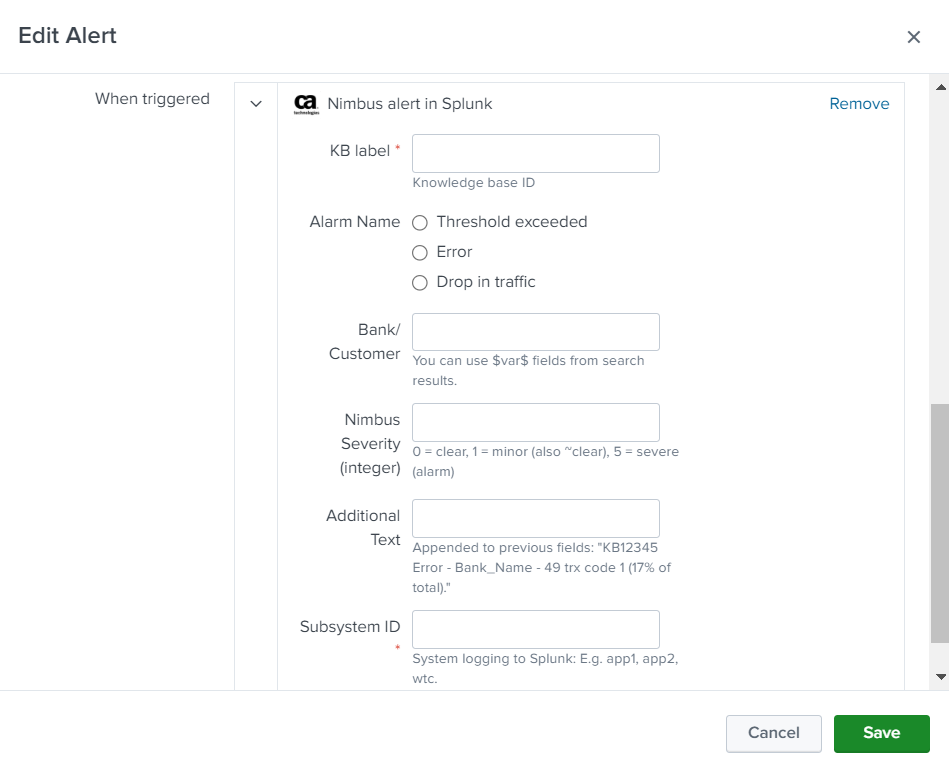
The custom add-on created for Splunk provides custom alert trigger functionality and is designed to send alerts to CA UIM using the 'nimalarm' utility. This add-on can be configured to monitor any type of data source within a Splunk environment, and when a specific event or condition occurs, it triggers an alert using 'nimalarm' to send it to the CA UIM system. The 'nimalarm' utility ensures that the alert is delivered in a timely and efficient manner, and can be customized to meet the specific needs of each user. With this add-on, users can proactively manage their data, detect and respond to issues quickly, and ensure that critical events are immediately communicated to the CA UIM system for further action. This can help users to improve their overall Splunk experience, and ensure that they are able to effectively manage their IT infrastructure.
0
(0)
Categories
Created By
Type
Downloads
Licensing
Splunk Answers
Resources